Sep 10, 2018 You have created your application. How to Get application ID and authentication key. To get the application Client Id and Key details. 1) From the App registrations in Azure Active Directory, select your application.
-->This article shows you how to create a new Azure Active Directory (Azure AD) application and service principal that can be used with the role-based access control. When you have code that needs to access or modify resources, you can create an identity for the app. This identity is known as a service principal. You can then assign the required permissions to the service principal. This article shows you how to use the portal to create the service principal. It focuses on a single-tenant application where the application is intended to run within only one organization. You typically use single-tenant applications for line-of-business applications that run within your organization.
Important
Instead of creating a service principal, consider using managed identities for Azure resources for your application identity. If your code runs on a service that supports managed identities and accesses resources that support Azure AD authentication, managed identities are a better option for you. To learn more about managed identities for Azure resources, including which services currently support it, see What is managed identities for Azure resources?.
Create an Azure Active Directory application
Let's jump straight into creating the identity. If you run into a problem, check the required permissions to make sure your account can create the identity.
Sign in to your Azure Account through the Azure portal.
Select Azure Active Directory.
Select App registrations.
Windows Server 2012 Foundation Edition Licensing Model. Windows Server 2012 Foundation is available to OEMs (Original Equipment Manufacturers) only and therefore can only be purchased at the time of purchasing a n new hardware server. Windows 2012 Foundation edition supports up to 15 users. Team foundation server 2012 license key generator no survey. Visual studio 2012 Product Key. The application offers programmers with the entire tools required to develop a software right from scratch. The application comes with a code editor application that supports IntelliSense. Along with that are integrated debugger units both on. This key's fingerprint is A04C 5E09 ED02 B328 03EB 6116 93ED 732E 9231 8DBA. Windows Server 2012 R2 Server Standard. Windows Server 2012 R2 Datacenter. The Courage Foundation is an international organisation that supports those who risk life or liberty to make significant contributions to the historical record. Apr 20, 2018 A utility to help create projects on Visual Studio Team Foundation Server with pre-populated sample content that includes source code, work items, iterations, service endpoints, build and release definitions based on a template you choose. The purpose of this system is to simplify working with the hands-on-labs, demos and other education material provided by the Microsoft Visual Studio.
Select New registration.
Name the application. Select a supported account type, which determines who can use the application. Under Redirect URI, select Web for the type of application you want to create. Enter the URI where the access token is sent to. You can't create credentials for a Native application. You can't use that type for an automated application. After setting the values, select Register.
You've created your Azure AD application and service principal.
Fable 3 product keygen. Feb 14, 2013 NO need to go anywhere. No shortened links. No waiting time. No Surveys to go through. No payment to be made MR7PR-G6JHM-HK6GQ-FQX3K-9QTWG:D. Jan 15, 2012 Free Fable 3 KW2HC-GQF3J-FBPBP-V4W64-YWYVD. We hope our friends are all staying safe during the Coronavirus situ. Bored at home?
Assign a role to the application
To access resources in your subscription, you must assign a role to the application. Decide which role offers the right permissions for the application. To learn about the available roles, see RBAC: Built in Roles.
You can set the scope at the level of the subscription, resource group, or resource. Permissions are inherited to lower levels of scope. For example, adding an application to the Reader role for a resource group means it can read the resource group and any resources it contains.
In the Azure portal, select the level of scope you wish to assign the application to. For example, to assign a role at the subscription scope, search for and select Subscriptions, or select Subscriptions on the Home page.
Select the particular subscription to assign the application to.
If you don't see the subscription you're looking for, select global subscriptions filter. Make sure the subscription you want is selected for the portal.
Select Access control (IAM).
Select Add role assignment.
Select the role you wish to assign to the application. For example, to allow the application to execute actions like reboot, start and stop instances, select the Contributor role. Read more about the available roles By default, Azure AD applications aren't displayed in the available options. To find your application, search for the name and select it.
Select Save to finish assigning the role. You see your application in the list of users with a role for that scope.
Your service principal is set up. You can start using it to run your scripts or apps. The next section shows how to get values that are needed when signing in programmatically.
Get values for signing in
When programmatically signing in, you need to pass the tenant ID with your authentication request. You also need the ID for your application and an authentication key. To get those values, use the following steps:
Select Azure Active Directory.
Firstly, Android Keystoremitigates unauthorized use of key material outside of the Android device by preventing extraction ofthe key material from application processes and from the Android device as a whole. This document goes over when and how to use the Android Keystoreprovider. Secondly,Android KeyStore mitigates unauthorized use of key material on the Android device by making appsspecify authorized uses of their keys and then enforcing these restrictions outside of the apps'processes. Security featuresAndroid Keystore system protects key material from unauthorized use. Java generate key pair programmatically.
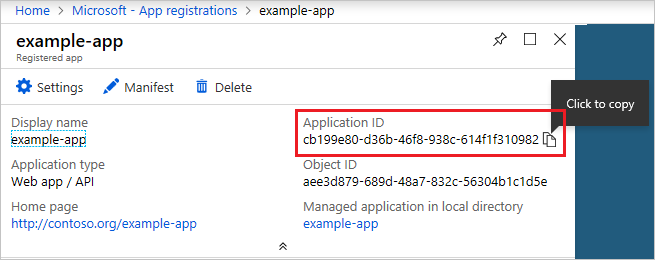
From App registrations in Azure AD, select your application.
Copy the Directory (tenant) ID and store it in your application code.
Copy the Application ID and store it in your application code.
Certificates and secrets
Daemon applications can use two forms of credentials to authenticate with Azure AD: certificates and application secrets. We recommend using a certificate, but you can also create a new application secret.
Upload a certificate
Azure Generation Client Id And App Key Fob
You can use an existing certificate if you have one. Optionally, you can create a self-signed certificate for testing purposes only. Open PowerShell and run New-SelfSignedCertificate with the following parameters to create a self-signed certificate in the user certificate store on your computer:
Windows 8.1 Product Key Generator is another software created by the Microsoft for the activating of Windows 8.1 OS. Since the product key is very important in activating this software, they had to develop a means of getting it. Windows 8.1 product key generator. Jan 12, 2020 Windows 8.1 Product Key Generator Full Cracked 2020. Windows 8.1 Product Key Generator Complete Cracked 2019 has been the whole next-generation working system. It turned the main decision OS for all, as a result of growing user-friendly and pleasing to your eye. The background came into life with interactive tiles. Windows 8.1 Activator + Product Key Generator Free Download 2019. Windows 8.1 Activator a good software for non-active windows. There are many types of window activator and reloader all over the world. But Generator is an authenticated and recommended generator for windows activated. It makes your windows registered. Windows 8.1 Product Key Generator can utilize to make the activator key like the Microsoft in the product key and can utilize most of the recent version.In contrast, users can use the utility in exceptionally in the mainstream since the user can use the inclusive kinds of methods. Mar 10, 2020 Windows 8.1 Product Key Generator Free 100% Working Lifetime Activator Windows 8.1 Product Key generator a great for activating Windows 8.1. A lot of users have been using it all around the globe. It moreover works as an activated version. Also, it includes new features and services improvements.
Export this certificate to a file using the Manage User Certificate MMC snap-in accessible from the Windows Control Panel.
Select Run from the Start menu, and then enter certmgr.msc.
The Certificate Manager tool for the current user appears.
To view your certificates, under Certificates - Current User in the left pane, expand the Personal directory.
Right-click on the cert you created, select All tasks->Export.
Follow the Certificate Export wizard. Do not export the private key, and export to a .CER file.
To upload the certificate:
Select Azure Active Directory.
From App registrations in Azure AD, select your application.
Select Certificates & secrets.
Select Upload certificate and select the certificate (an existing certificate or the self-signed certificate you exported).
Select Add.
After registering the certificate with your application in the application registration portal, you need to enable the client application code to use the certificate.
Create a new application secret
If you choose not to use a certificate, you can create a new application secret.
Select Certificates & secrets.
Select Client secrets -> New client secret.
Provide a description of the secret, and a duration. When done, select Add.
After saving the client secret, the value of the client secret is displayed. Copy this value because you won't be able to retrieve the key later. You will provide the key value with the application ID to sign in as the application. Store the key value where your application can retrieve it.
Configure access policies on resources
Keep in mind, you might need to configure addition permissions on resources that your application needs to access. For example, you must also update a key vault's access policies to give your application access to keys, secrets, or certificates.
- In the Azure portal, navigate to your key vault and select Access policies.
- Select Add access policy, then select the key, secret, and certificate permissions you want to grant your application. Select the service principal you created previously.
- Select Add to add the access policy, then Save to commit your changes.
Required permissions
You must have sufficient permissions to register an application with your Azure AD tenant, and assign to the application a role in your Azure subscription.
Check Azure AD permissions

Select Azure Active Directory.
Note your role. If you have the User role, you must make sure that non-administrators can register applications.
In the left pane, select User settings.
Check the App registrations setting. This value can only be set by an administrator. If set to Yes, any user in the Azure AD tenant can register an app.
If the app registrations setting is set to No, only users with an administrator role may register these types of applications. See available roles and role permissions to learn about available administrator roles and the specific permissions in Azure AD that are given to each role. If your account is assigned the User role, but the app registration setting is limited to admin users, ask your administrator to either assign you one of the administrator roles that can create and manage all aspects of app registrations, or to enable users to register apps.
Check Azure subscription permissions
In your Azure subscription, your account must have Microsoft.Authorization/*/Write access to assign a role to an AD app. This action is granted through the Owner role or User Access Administrator role. If your account is assigned the Contributor role, you don't have adequate permission. You will receive an error when attempting to assign the service principal a role.
To check your subscription permissions:
Search for and select Subscriptions, or select Subscriptions on the Home page.
Select the subscription you want to create the service principal in.
If you don't see the subscription you're looking for, select global subscriptions filter. Make sure the subscription you want is selected for the portal.
Select My permissions. Then, select Click here to view complete access details for this subscription.
Select View in Role assignments to view your assigned roles, and determine if you have adequate permissions to assign a role to an AD app. If not, ask your subscription administrator to add you to User Access Administrator role. In the following image, the user is assigned the Owner role, which means that user has adequate permissions.
Next steps
- To learn about specifying security policies, see Azure Role-based Access Control.
- For a list of available actions that can be granted or denied to users, see Azure Resource Manager Resource Provider operations.
The following error codes could be returned by an operation on an Azure Key Vault web service.
HTTP 401: Unauthenticated Request
401 means that the request is unauthenticated for Key Vault.
A request is authenticated if:
- The key vault knows the identity of the caller; and
- The caller is allowed to try to access Key Vault resources.
There are several different reason why a request may return 401.
No authentication token attached to the request.
Here is an example PUT request, setting the value of a secret:
The 'Authorization' header is the access token that is required with every call to the Key Vault for is mandatory. The value is important for the token provider because it scopes the token for its intended use. The resource for all tokens to access a Key Vault is https://vault.keyvault.net (with no trailing slash).
The token is expired
Tokens are base64 encoded and the values can be decoded at websites such as http://jwt.calebb.net. Here is the above token decoded:
We can see many important parts in this token:
- aud (audience): The resource of the token. Notice that this is https://vault.azure.net. This token will NOT work for any resource that does not explicitly match this value, such as graph.
- iat (issued at): The number of ticks since the start of the epoch when the token was issued.
- nbf (not before): The number of ticks since the start of the epoch when this token becomes valid.
- exp (expiration): The number of ticks since the start of the epoch when this token expires.
- appid (application ID): The GUID for the application ID making this request.
- tid (tenant ID): The GUID for the tenant ID of the principal making this request
It is important that all of the values be properly identified in the token in order for the request to work. If everything is correct, then the request will not result in 401.
Troubleshooting 401
401s should be investigated from the point of token generation, before the request is made to the key vault. Generally code is being used to request the token. Once the token is received, it is passed into the Key Vault request. If the code is running locally, you can use Fiddler to capture the request/response to https://login.microsoftonline.com. A request looks like this:
The following user-supplied information mush be correct:
- The key vault tenant ID
- Resource value set to https%3A%2F%2Fvault.azure.net (URL encoded)
- Client ID
- Client secret
Ensure the rest of the request is nearly identical.
If you can only get the response access token, you can decode it (as shown above) to ensure the tenant ID, the client ID (app ID), and the resource.
HTTP 403: Insufficient Permissions
HTTP 403 means that the request was authenticated (it knows the requesting identity) but the identity does not have permission to access the requested resource. There are two causes:
- There is no access policy for the identity.
- The IP address of the requesting resource is not whitelisted in the key vault's firewall settings.
HTTP 403 often occurs when the customer's application is not using the client ID that the customer thinks it is. That usually means that the access policies is not correctly set up for the actual calling identity.
Troubleshooting 403
First, turn on logging. For instructions on how to do so, see Azure Key Vault logging).
Once logging is turned on, you can determine if the 403 is due to access policy or firewall policy.
Error due to firewall policy
Azure App Client Id
'Client address (00.00.00.00) is not authorized and caller is not a trusted service'
There is a limited list of 'Azure Trusted Services'. Azure Web Sites are not a Trusted Azure Service. For more information, see the blog post Key Vault Firewall access by Azure App Services.
You must add the IP address of the Azure Web Site to the Key Vault in order for it to work.
If due to access policy: find the object ID for the request and ensure that the object ID matches the object to which the user is trying to assign the access policy. There will often be multiple objects in the AAD which have the same name, so choosing the correct one is very important. By deleting and re-adding the access policy, it is possible to see if multiple objects exist with the same name.
Get Azure Client Id
In addition, most access policies do not require the use of the 'Authorized application' as shown in the portal. Authorized application are used for 'on-behalf-of' authentication scenarios, which are rare.
HTTP 429: Too Many Requests
Throttling occurs when the number of requests exceeds the stated maximum for the timeframe. If throttling occurs, the Key Vault's response will be HTTP 429. There are stated maximums for types of requests made. For instance: the creation of an HSM 2048-bit key is 5 requests per 10 seconds, but all other HSM transactions have a 1000 request/10 seconds limit. Therefore it is important to understand which types of calls are being made when determining the cause of throttling.In general, requests to the Key Vault are limited to 2000 requests/10 seconds. Exceptions are Key Operations, as documented in Key Vault service limits
Troubleshooting 429
Throttling is worked around using these techniques:
Reduce number of requests made to the Key Vault by determining if there are patterns to a requested resource and attempting to cache them in the calling application.
When Key Vault throttling occurs, adapt the requesting code to use a exponential backoff for retrying. The algorithm is explained here: How to throttle your app
If the number of requests cannot be reduced by caching and timed backoff does not work, then consider splitting the keys up into multiple Key Vaults. The service limit for a single subscription is 5x the individual Key Vault limit. If using more than 5 Key Vaults, consideration should be given to using multiple subscriptions.
Azure Generation Client Id And App Key Fob
Detailed guidance including request to increase limits, can be find here: Key Vault throttling guidance